What kind of IM security functionality is available from the Blue Coat ProxySG?
Administrators can control IM functionality such as:
- Block File Transfers;
- Search for keywords;
- Limit chatroom access on a user or global basis;
- Instant Messaging messages can be monitored or logged (your boss is watching) =]
As a proxy the BC ProxySG can:
- Allow selected protocols;
- Establish authentication rules for using IM services;
- Allow or deny attachments by file type;
- Allow or deny chat activity;
- Filter Keywords (my boss is the best);
- Block access to IM services by user or other means.
- Block encrypted IM services, because you do not know what information is being transmitted.
Wednesday, May 27, 2009
Monday, May 25, 2009
Analysing 401 authentication on the Blue Coat ProxySG
When a client attempt to access a website via the proxy the OCS can send to the client an authentication challenge. The response from the OCS includes a 401 code indicating either the authentication credentials from the user has failed or the user must send credentials for the requested resources. Note that a 401 message is different to a 407 message. 407 is from the proxy and 401 is from the OCS. Thus you may receive a 401 message even after you have successfully authenticated in response to a 407 message.
Below are the logs of client requests to www.google.com on the Blue Coat. You can see the initial 407 response to the proxy challenge:
2009-05-26 07:24:31 4 1.1.1.1 - - authentication_failed PROXIED "none" - 407 TCP_DENIED GET - http www.google.com 80 / - - "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 1095 352 -
2009-05-26 07:24:37 524 1.1.1.1 joe - - PROXIED "none" - 302 TCP_NC_MISS GET text/html;%20charset=UTF-8 http www.google.com 80 / - - "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 622 437 -
2009-05-26 07:24:39 536 1.1.1.1 joe - - PROXIED "none" - 200 TCP_NC_MISS GET text/html;%20charset=UTF-8 http www.google.com.au 80 / - - "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 4253 407 -
2009-05-26 07:24:40 530 1.1.1.1 joe - - PROXIED "none" http://www.google.com.au/ 200 TCP_MISS GET image/gif http www.google.com.au 80 /images/close_sm.gif - gif "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 380 543 -
2009-05-26 07:24:40 538 1.1.1.1 joe - - PROXIED "none" http://www.google.com.au/ 200 TCP_MISS GET image/gif http www.google.com.au 80 /images/chrome_48.gif - gif "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 2756 544 -
2009-05-26 07:24:40 548 1.1.1.1 joe - - PROXIED "none" http://www.google.com.au/ 200 TCP_MISS GET image/gif http www.google.com.au 80 /images/modules/buttons/g-button-chocobo-basic-2.gif - gif "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 619 575 -

Below are the logs of client requests to www.google.com on the Blue Coat. You can see the initial 407 response to the proxy challenge:
2009-05-26 07:24:31 4 1.1.1.1 - - authentication_failed PROXIED "none" - 407 TCP_DENIED GET - http www.google.com 80 / - - "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 1095 352 -
2009-05-26 07:24:37 524 1.1.1.1 joe - - PROXIED "none" - 302 TCP_NC_MISS GET text/html;%20charset=UTF-8 http www.google.com 80 / - - "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 622 437 -
2009-05-26 07:24:39 536 1.1.1.1 joe - - PROXIED "none" - 200 TCP_NC_MISS GET text/html;%20charset=UTF-8 http www.google.com.au 80 / - - "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 4253 407 -
2009-05-26 07:24:40 530 1.1.1.1 joe - - PROXIED "none" http://www.google.com.au/ 200 TCP_MISS GET image/gif http www.google.com.au 80 /images/close_sm.gif - gif "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 380 543 -
2009-05-26 07:24:40 538 1.1.1.1 joe - - PROXIED "none" http://www.google.com.au/ 200 TCP_MISS GET image/gif http www.google.com.au 80 /images/chrome_48.gif - gif "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 2756 544 -
2009-05-26 07:24:40 548 1.1.1.1 joe - - PROXIED "none" http://www.google.com.au/ 200 TCP_MISS GET image/gif http www.google.com.au 80 /images/modules/buttons/g-button-chocobo-basic-2.gif - gif "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; GTB5; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 1.1.4322; InfoPath.1; .NET CLR 2.0.50727)" 203.41.5.249 619 575 -

Sunday, May 24, 2009
Blue Coat ProxySG - How to find objects in the cache of the appliance.
There are a number of ways to determine if an object is being cached by the proxysg. Two methods are:
1. Querying the cache directly.
2. Inspecting the logs.
1. Querying the cache directly:
To find/view/see if an object is being cached we can query the cache directly by browsing to the absolute path of the object without the specification of the protocol. For example, if we were to browse to www.cisco.com we can find the object "home.min.js" is requested. The absolute path of this object is:
http://www.cisco.com/web/fw/j/home.min.js
Using this information we verify if the Blue Coat proxySG is caching this object. Simply attach the absolute path of the object to the Blue Coat URL minus the protocol. For example:
https://proxysg ip address:8082/CE/Info/http/www.cisco.com/web/fw/j/home.min.js
If the object is found then you should see a page with statistics regarding the object such as that below:
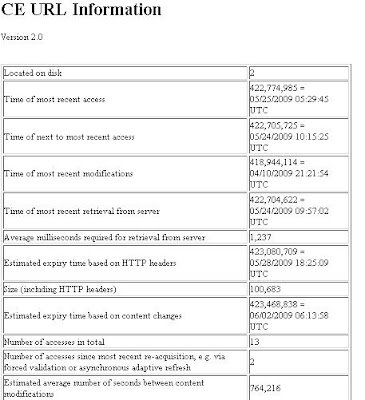
2. Inspecting the logs.
An object can also be verified to be in the cache by inspecting or looking at the logs. To do this start a tail in the management console or on the CLI:
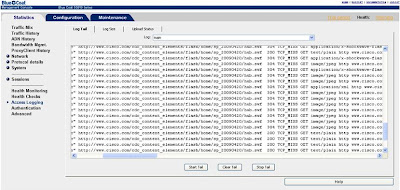
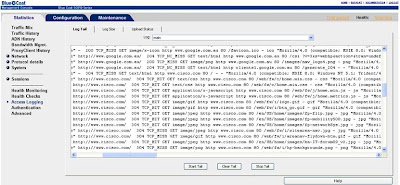
In this scenario we have browsed to Cisco.com having been there before. As you can see we have many "HITS" indicating the object is being served from the proxy. There are also misses indicating the corresponding object has not been cached.
1. Querying the cache directly.
2. Inspecting the logs.
1. Querying the cache directly:
To find/view/see if an object is being cached we can query the cache directly by browsing to the absolute path of the object without the specification of the protocol. For example, if we were to browse to www.cisco.com we can find the object "home.min.js" is requested. The absolute path of this object is:
http://www.cisco.com/web/fw/j/home.min.js
Using this information we verify if the Blue Coat proxySG is caching this object. Simply attach the absolute path of the object to the Blue Coat URL minus the protocol. For example:
https://proxysg ip address:8082/CE/Info/http/www.cisco.com/web/fw/j/home.min.js
If the object is found then you should see a page with statistics regarding the object such as that below:

2. Inspecting the logs.
An object can also be verified to be in the cache by inspecting or looking at the logs. To do this start a tail in the management console or on the CLI:


In this scenario we have browsed to Cisco.com having been there before. As you can see we have many "HITS" indicating the object is being served from the proxy. There are also misses indicating the corresponding object has not been cached.
Subscribe to:
Posts (Atom)